Hello, recently I was trying to figure out neat ways of utilizing my YubiKey. I am fond of using Linux for safe environments and thought that a YubiKey would be a neat way to create a unique method of adding 2FA. Yubikey can be natively integrated into SUDO and login 2FA methods.
Installation guide can be found here:
https://support.yubico.com/hc/en-us/articles/360016649039-Installing-Yubico-Software-on-Linux
I installed the required software using sudo apt install yubikey-manager. Then I enabled the pcscd service, which according to their documentation: “pcscd is the daemon program for pcsc-lite and the MuscleCard framework. It is a resource manager that coordinates communications with smart card readers and smart cards and cryptographic tokens that are connected to the system.”
I am not going to lie, this process of getting the Yubikey working was a royal pain. But after injecting logs into the scdaemon configuration, (scdaemon is used to manage smartcards. It is usually invoked by gpg-agent and in general not used directly) I was able to determine that I wasn’t able to invoke gpg --card-status due to permissions issues. I was able to find the best config to use:
reader-port Yubico Yubi
disable-ccid
debug-level guruApparently, scdaemon didn’t have permissions to access the USB device; instead, this allowed access via the pcscd service.
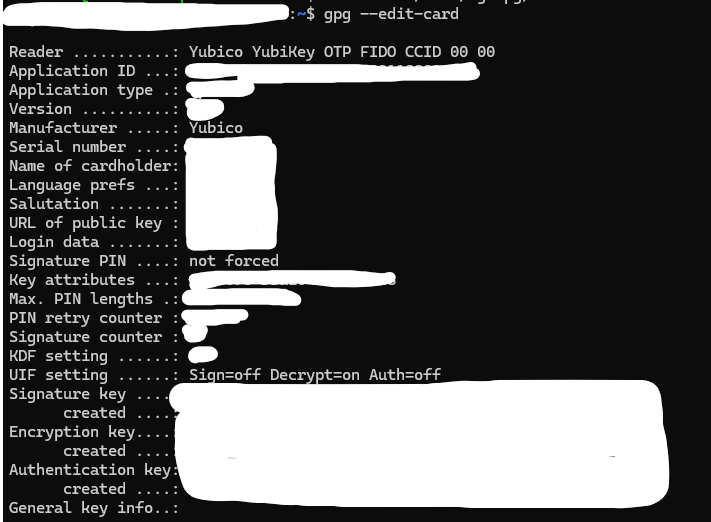
Lastly, I used gpg --edit-card to create my encryption key and to modify the UIF setting (User Interaction Flag, which allows touch) specifically for decryption. I won’t go into detail exactly how I plan on using this, but I can say my use case is 100% operational now!